Is Telegram’s Privacy Shift Driving Extremists Toward SimpleX?

On September 23, 2024, 404 Media reported that Telegram announced changes to its terms of service. In an update to its privacy policy, Telegram stated that it will now share IP addresses and phone numbers with law enforcement authorities in response to valid orders. There has been plenty of speculation and growing uncertainty around the safety of Telegram among terrorist and violent extremist networks that use it. There was a real fear among these threat actors that Telegram might start cooperating with authorities, and today that fear became a reality. For weeks now, there has been increased discussion around the use of alternative secure communication platforms such as Session, Signal, Threema, Matrix, etc. One platform that has seen a migration of Telegram chat and channel networks is SimpleX, which we will explore today.
The migration of terrorists and violent extremists between online platforms isn’t unique to Telegram, nor is it the first time threat actors have moved away from Telegram. Over the years, as governments and tech companies have cracked down on terrorist and violent extremist use of the internet, these groups have been forced to find new places to communicate and organize. However, moving to a new platform is rarely easy or successful. Threat actors, like the rest of us, tend to stick with what they are familiar with unless something forces them to change. Yet, for privacy-focused individuals—whether extremists or simply those trying to avoid surveillance—platforms like SimpleX, which offer decentralized technology, encryption, and stronger anonymity than something like Telegram, provide a safer option for those prioritizing operational security. For terrorists and violent extremists looking to avoid detection, SimpleX Chat provides significant advantages over Telegram, largely due to its design and features that prioritize privacy and anonymity. SimpleX offers end-to-end encryption by default for all messages, whereas Telegram only encrypts conversations in its "secret chats." Regular chats on Telegram, while encrypted on their servers, are still accessible by the platform itself, users, and the API. SimpleX provides a much stronger layer of security because no one—not even the company behind it—can access those conversations. SimpleX also has a significant advantage when it comes to protecting metadata—the information that can reveal who you’re talking to, when, and how often. SimpleX is designed with privacy at its core, minimizing the amount of metadata collected and ensuring that any temporary data necessary for functionality is not retained or linked to identifiable users. Another key difference is in how users sign up for these platforms. Telegram requires a phone number for registration, which automatically ties an account to an identifiable piece of information. In contrast, SimpleX doesn’t require any personal information—no phone numbers, no emails—which is an operational security advantage. Additionally, you can join a channel anonymously as an observer or join with your username to be more active.
However, added layers of security can impact some functionalities. Telegram has been successfully used by threat actors for network building, propaganda dissemination, and planning attacks. However, propaganda and network building will be less straightforward on SimpleX. For example, a group or channel on SimpleX is only joinable if the owner is online. This means you cannot always instantly access communities. Furthermore, if an owner becomes inactive, loses their phone without a backup of their SimpleX account, or is arrested, no new members can join until the owner logs back on.
Another limitation of SimpleX that can affect propaganda and multimedia archives is how messages disappear. Specifically, the previous 100+ messages sent within a certain time frame before a new member joins are not visible to that new member. Additionally, files shared on SimpleX are only stored on the server for two days. If a file is shared two days or more before a new member joins the group or channel, they cannot see the file, even if the message containing the file is sent within the 100-message range.
Information on SimpleX is ephemeral, which is an operational security advantage. However, this also impacts cultural construction and propaganda dissemination. For content to survive on this platform, users will need to create mirrors of channels and archive posts and multimedia immediately. While there are benefits to this type of platform architecture, there are also downsides in terms of large-scale terrorist and violent extremist migration. SimpleX might serve as a suitable platform for chats and private communications, but the impact of channels will be limited without an intermediary platform to host and store content in perpetuity.
Scale of Migration
As it stands, there are approximately a dozen chats and channels that I am tracking on SimpleX. All of these are part of a network of Telegram threat actors who heavily focus on operational and personal security. It is not surprising that these individuals are leading the push for migration, as this conversation has been ongoing for a few months. I used Extrac to examine the chatter (92 posts) related to the use of SimpleX.
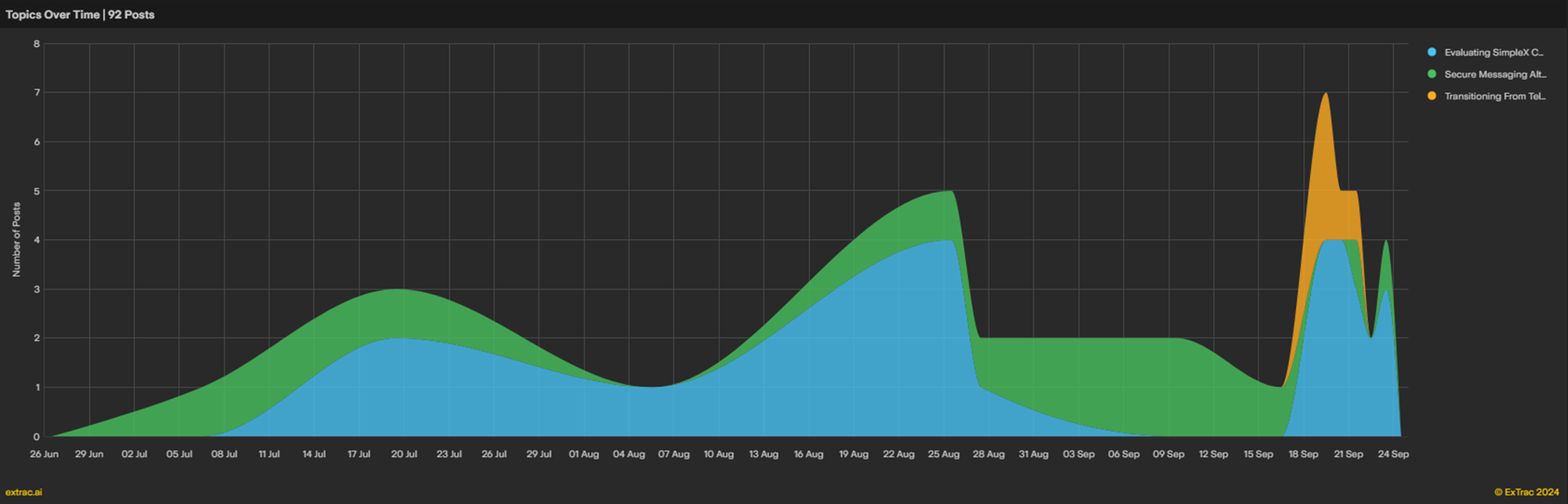
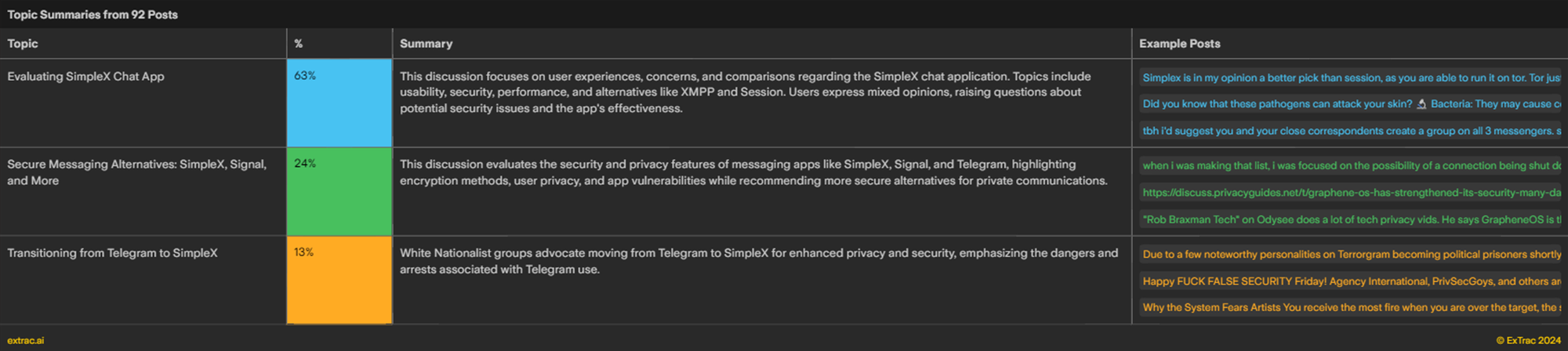
We can see that the conversation started in June 2024, with actors on Telegram discussing and evaluating the security and privacy features of Telegram alternatives. The conversation focused on encryption methods, user privacy, and platform vulnerabilities. In July, the conversation shifted to evaluating SimpleX specifically. The discussion centered on user experiences with the platform, its usability, performance, and comparisons to other alternatives like XMPP and Session messaging. It wasn't until September 18th that administrators of the aforementioned network advocated for migration from Telegram to SimpleX, highlighting the risks and vulnerabilities posed by Telegram.
According to their own posts on the subject, they claim that since September 18th—when these chats and channels were created six days ago—700 users have joined their digital assets on Telegram, with 350 active users currently chatting..
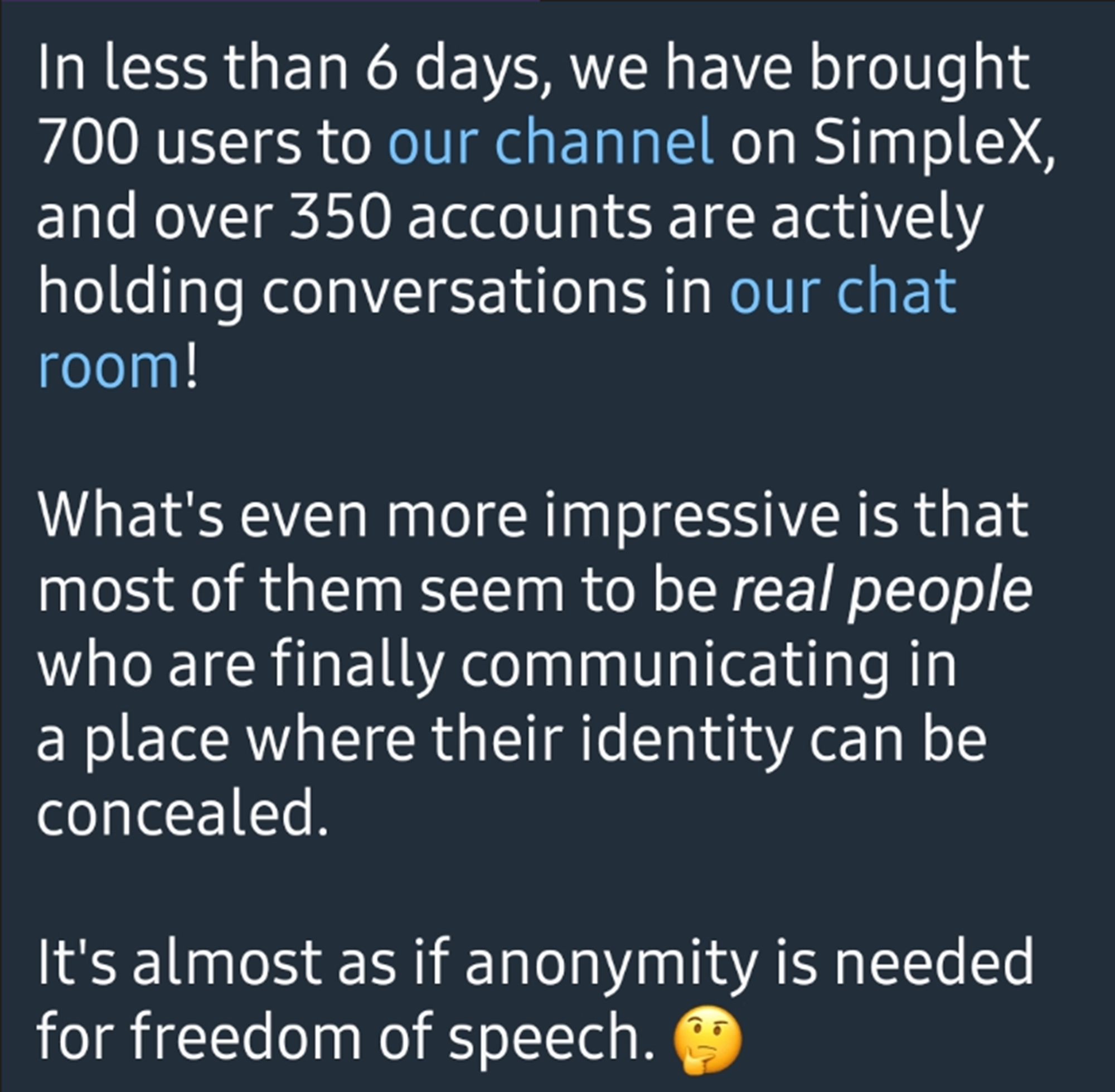
In the grand scheme of things, this is a drop in the bucket of Telegram chats and channels and is in no way an indication of a full-scale migration. Experimentation and attempts like these are common in threat actor spaces, especially following significant arrests or shifts in platform policies.
In conclusion, while Telegram’s decision to share user data with authorities has triggered some movement toward platforms like SimpleX, we’re not witnessing a mass exodus just yet. The shift has been led by those most focused on maintaining their privacy and operational security, but it’s still in the early stages and remains more of a trial than a full migration. SimpleX offers attractive privacy features, but it also comes with propagandistic trade-offs. The platform’s design, while excellent for secure conversations, makes it harder for groups to spread propaganda or build large networks, as its limitations around message visibility and file retention complicate how information is shared and stored within violent extremist milieus.
SimpleX might be a good fit for smaller, security-focused groups, but it has limitations that could impact its broader appeal. So while we’re seeing attempts at change, it’s too soon to say whether platforms like SimpleX will replace Telegram in the long run—or if they’ll just become another tool tested in the ever-evolving threat actor toolkit.