When 'Community' Means Cruelty: An Introduction to the Criminal Networks and Behaviors of The Community, Comm, Com, and 764

CONTENT WARNING: This article contains references to sextortion, child sexual exploitation, self-harm, violent extremism, terrorism, gore, eating disorders, kidnapping and rape.
In January of this year, I published an article with some colleagues on a network of threat actors called 764. You can find my initial writing about this topic here in this GNET article. As a refresher, 764 is an online child extortion group created by a Discord user named Brad764. Inspiration for 764 was drawn from another Discord community known as “CVLT” that force children to perform sexual acts on camera and later using the recordings for sextortion. Unlike Cvlt, 764 does not only leverage the sextortion of minors but also animal torture, incest, rape, self-harm, and bestiality. 764 forces victims to carry out four key types of harm that may be recorded and shared on social media platforms or disseminated internally. These include forced drug use and self-harm, such as non-suicidal self-injury with blades or needles, asphyxiation or burning. They also regularly encourage people suffering from mental health problems to kill themselves on camera or commit mass shootings. New members are also encouraged to engage in animal abuse, being forced to injure or kill personal pets or other animals. Sextortion and CSAM are also key dimensions of 764; victims are groomed to share intimate images to be used to subsequently sextort and doxx them, creating ‘LoreBooks’ filled with sexually explicit content to be shared with victims’ friends and family if they don’t comply.
What is “the comm”?
The 764 community does not exist in isolation, rather it is hyper- connected to a wider network of hybridized threats and threat actors called Comm aka the Community. Comm or "The Community" is a nebulous network of Discord and Telegram channels administered mostly by minors involved in CSAM, sextortion, cyber stalking, hacking, swatting, gore, terrorism, school shootings, drugs, bricking, arson, and scams. The 764 network is the subset of Comm involved in sextortion. The group is not only increasingly violent, but also audacious enough to document and disseminate all their activities.
Here is how an insider from Comm describes the space in a Telegram post:
“The comm”, also known as Comm, Com, or The Community, is a network of different child pornography and child extortion rings. Sigma Enthusiast and many of his good friends such as Island Monkey, Kush, MK Ultra, Kenvy, Gorebutcher, Connor (“Holy” Emperor Serpentarius), Brad, Rex Mensis, Riley764, Kaleb Merritt, Lalo, and many others have all been active participants in comm-affiliated groups such as 764, CVLT, Legion, Anarchy, Tempel Ov Blood, Deresistance, SCUMZ, and 6996. There are others but those are at this point the main ones. Not only do people who are part of “comm” affiliated groups like to groom minors (mostly teenage girls, but in some cases also teenage boys) but they also like to extort these minors and make them hurt themselves, often severely. Some, such as Kaleb Merritt, have even went as far as doing these things outside of the internet in addition to on the internet. Many of the groomers are teenagers themselves, which does not excuse their behavior because these are the sorts of things that are unacceptable regardless of how old the victims and perpetrators are. Teenaged groomers will often bring other teenagers into these groups.
As Joseph Cox and Krebs on Security noted in past reporting the Comm has existed for a while now, with the InfoSec community being aware of the network for their SIM Swapping, swatting, and cyber criminal activities. Comm has existed on other messaging platforms like Team Speak and Kik; however, the current iteration of the network is primarily on Discord with a growing population of users on Telegram dubbed “telecom”. They use these messaging platforms to engage in widespread criminal acts.
According to an FBI affidavit, Comm consist of a geographically diverse group of individuals organized in various subgroups all of whom coordinate through online communication applications such as discord and telegram to engage in various types of criminal activity to include corporate intrusion, SIM swapping, cryptocurrency theft, commissioning in real life violence, and swatting. Comm is not a homogeneous community, rather it is a memeplex of digital criminal networks overlapping with gaming subculture.
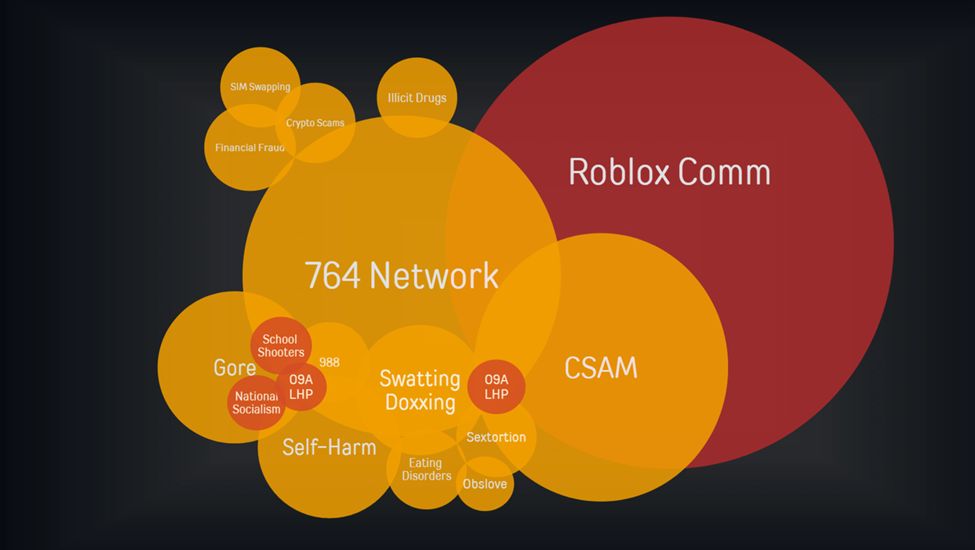
There is a fluidity between overlapping networks that can be represented properly by Venn diagrams. Individuals can be part of multiple communities simultaneously. Participation within these communities is also fluid. An individual from the swatting community might not be interested in consuming, producing or disseminating CSAM, however they have no qualms in offering swatting or doxxing and services in another user’s efforts to obtain material from a minor through sextortion, which results from the use of their swatting and doxxing services. Similarly, there is a fluidity between the criminal activity in Comm and the national security threats also present in Comm. An example which I plan to cover in later posts is the growing movement within 764 networks pushing minors from digital criminality and activities to off-line criminal and violent acts due to the influence of domestic and transnational terrorism violent extremist networks like MKY (a.k.a. maniac murder cult), Order of Nine Angles, and Satanic Front (the current rebrand of Temple ov Blood).
Comm and Gaming
A large segment of the Comm network is facilitated through the Roblox community. Roblox is an online game creator system where most of the content is created by amateur game creators and individuals in Roblox studio. These games are published publicly to the community using simple tools. These games can then be played by children worldwide often online together through a phone or tablet or via web browser.
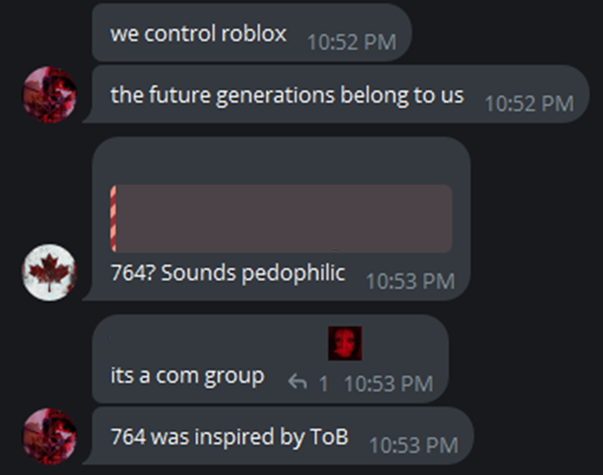
The average age of a Roblox user is between eight and 13 years old. This is also a pool from which members of sextortion networks will seek to recruit individuals into spaces where these minors can be exploited and victimized. Roblox is also a place where minors will be able to experience taboo subjects as they can get invited to games that reflect or represent harmful content such as simulating mass shootings, concentration camps, or other violent scenarios. Another popular game within Comm is Minecraft, which is a predecessor of Roblox. The aesthetics of the games are similar and there is crossover between Minecraft and Roblox players. Minors who seek out these games are preyed upon by members of Comm and are targets for recruitment into the Discord and Telegram networks. A member of the 764 networks will gain more notoriety the younger the victim they are grooming.
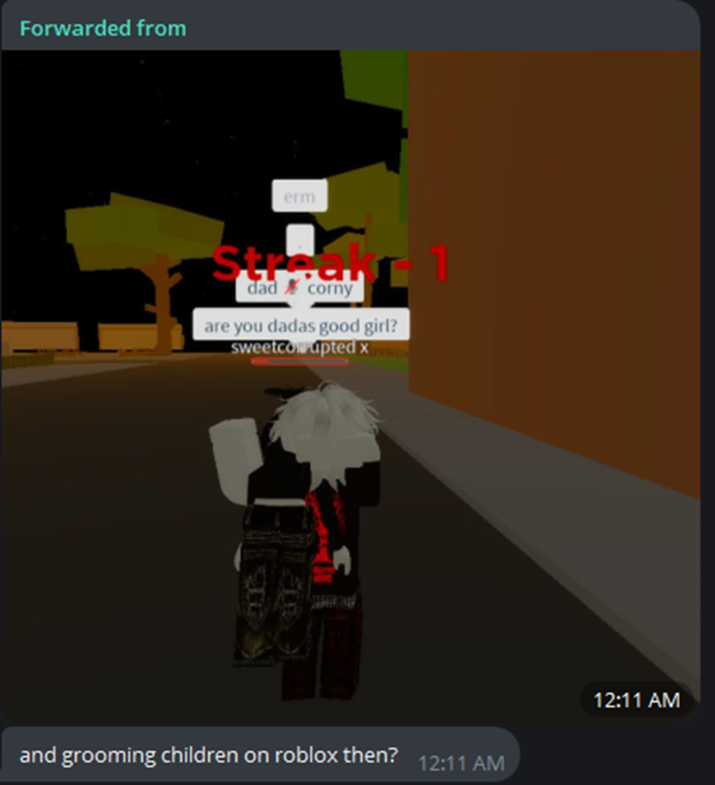
Roblox provides a perfect environment for them to predate upon minors. This poses a challenge for parents, as it is not abnormal to see your child playing these games on their computer or their tablets, nor would it be abnormal for them to be talking to people in game with them. The threat posed by the 764 network is one that requires parents to be not only aware of their children’s activities but of the content of the games that they are playing and the people they are playing with.
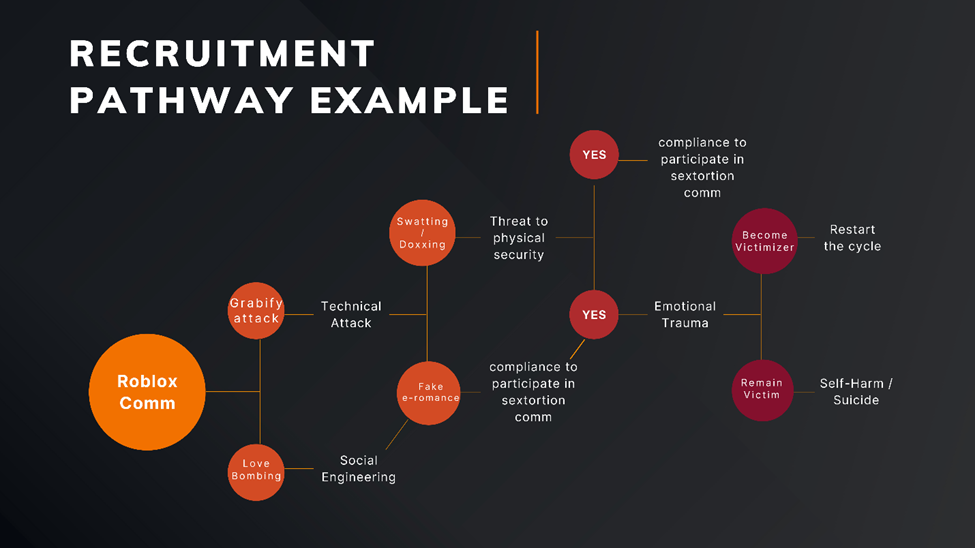
One of the ways that minors are lured into spaces controlled by the 764 network is by being offered access to in game currencies such as Robux, Discord Nitro (a premium server status) and Telegram Premium.
Figure 5 Predator asking victim how much Robux they want for doing what they requested.
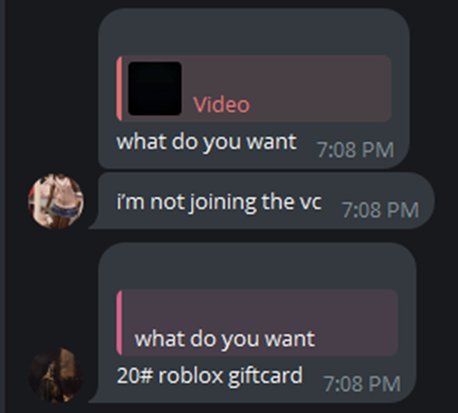
Minors do not have access to the capacity to purchase in game currencies as they do not have a credit card. Therefore, if they want to access funds to obtain vanity items and statuses within the games or communication applications that they use, they must either rely on their parents or via donations from strangers they need online. Members of the 764 networks will regularly offer Robux, Nitro or Premium as a way of luring individuals to their servers.

As soon as minors click the link to join these servers, it is likely too late. Often, the Telegram or Discord links that are shared as part of the grooming or recruitment process are actually IP loggers (e.g., Grabify is a popular choice). Documents shared in these channels or with individuals, such as PDFs, often contain keyloggers. This provides the members of the 764 networks with the leverage they need to begin exerting power over the people they target. Part of the control comes through sextortion. These predators use doxxing or social engineering to control minors who might not be aware of digital security practices, using swatting, bricking, or real-life violence. It is important to highlight that within these communities, sharing personally identifiable information is common practice, as is doxxing individuals in the community. There are entire channels, archives, documents, and doxxbins (sites to anonymously leak personally identifiable information about individuals) dedicated to both real and fabricated personally identifiable information about victims and victimizers in the 764 networks. The threat of using this information for real-life consequences is an important leverage in the sextortion process.
Another way control is exerted is that to join these private servers, you need to share child sexual exploitation material or demonstrate evidence of recent self-harm. Most individuals within these spaces regularly state that they are not subject to the law in terms of sharing child pornography or material obtained through sextortion, as they are themselves minors and cannot be prosecuted. To that end, the majority of the community do not realize what they are doing is, in fact, illegal. Nevertheless, the high-profile arrests of foundational members of this network and the long prison sentences they have received, as well as the recent interest in the 764 networks by law enforcement, have had a chilling effect on some individuals in these spaces as they realize that their actions might lead to long prison sentences.
Clout Chasing and Nihilism
Comm and the 764 network have another important form of currency: clout. Leaders and influencers in 764 regularly state both in chats and via court documents that clout and power were central to their participation in these criminal activities. Due to the central role of clout within these spaces, it is not surprising that access to vanity tags or in-game cosmetics plays a central role for those who are not only seeking to recruit and groom victims but are also avid gamers and players of these games.
Part of how they attract victims in the first place is by having access to premium in-game items and all the vanity items for servers. This is also why they give themselves titles and administrative access across all the chats and channels. These vanity tags are a way for users to demonstrate their power and influence within the network. Therefore, those who do not have these vanity items are culturally ranked lower within the hierarchy of the network. For example, a Telegram chat seeking to attract new users promoted a Telegram Premium Giveaway in community channels and chats on Telegram.
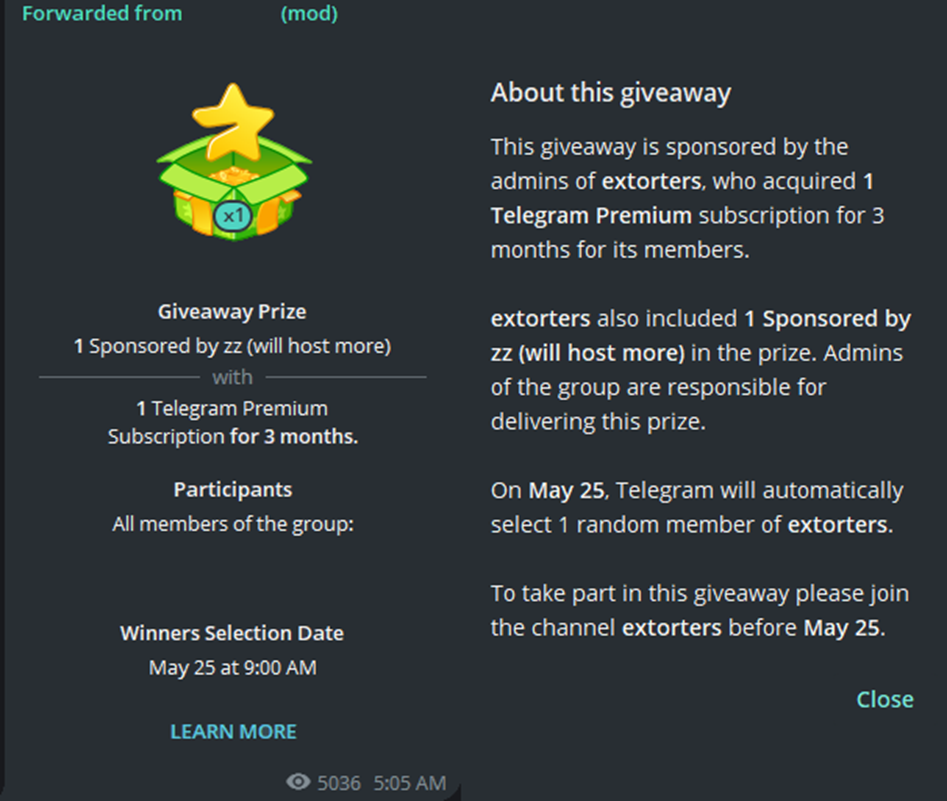
Though aesthetics, clout, and vanity items may appear superficial and insignificant, they are not for those who exist within comm. Success within this ecosystem is measured by one’s ability to victimize people; it is measured by the size of one’s following. The higher your body count and follower count, the more notoriety you have within the ecosystem. Consequently, the more influential and powerful you are, the more influence and power you can exert over new members joining. This is made clear in the court records of Cadenhead, who states that the reasoning behind his nihilistic behavior and crimes was that his violent and criminal actions gave him power, made him a “cult leader,” and gave him influence and a “harem of e-girls.” He was online what he believed he could not be offline; this is true for most of the predators and threat actors in this ecosystem.
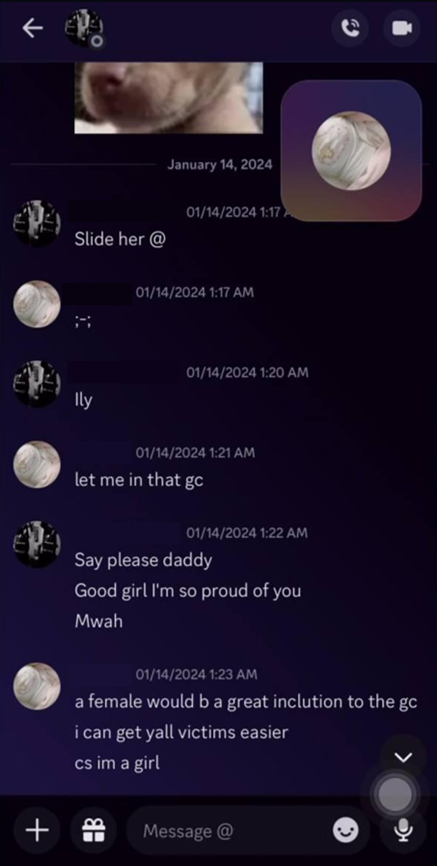
This means those with the most power, influence, and clout are those whose names appear in: fansigns (predator's name written on a victim’s body in marker or via vandalizing private property with spray paint), bloodsigns (predator's name written on the victim’s body with their blood), and cutsigns (predator's name carved into a victim’s body with a blade), are also those who have likely victimized the most minors. These minor predators have been responsible for grooming multiple individuals, forcing individuals to commit crimes, forcing individuals to commit suicide, or participating in acts of animal cruelty and abuse. Furthermore, compounding harms upon a single individual gives you more clout as well. For example, if you can recruit and groom someone suffering from an eating disorder, the skinnier the individual is when they do a cutsign or a bloodsign, the more “clout points” you win in your comm. There is a nihilistic banality to the malevolent actions and sinister crimes that these minors are committing against each other for internet points, digital currency, and the pleasure they take in preying upon vulnerable individuals. Simply put, the violence they commit is for the sake of violence itself.
I do want to highlight that these are only some examples of how targets are selected and compromised. Additionally, I want you, my audience, to note that there are multiple variations in how threats are hybridized in comm. As you follow along in my exploration of comm and 764, my next piece in this series will examine the national security threat posed by 764 as it overlaps with accelerationist threat actors/networks, such as: the Order of Nine Angles, Temple ov Blood, Маньяки: культ убийства (a.k.a М.К.У., МКУ, Maniac Murder Cult, MCC) and others. These accelerationists seek to take minors from these networks and move from cyber criminality to offline criminality and/or acts of stochastic violence.