The Pillars of the Com Network

The Com Ecosystem
I know some of you were expecting Part 5 in my series of manifestos from the Com Network. However, prior to that post I believe I owe you all an updated explanation of what is the Com Network, how it functions as a radicalizing and mobilizing milieu and its three main pillars. Groups I have discussed like 764, No lives Matter, Maniacs Murder Cult, Satanic Front, do not exist in isolation, rather they are hyper-connected to a wider network of hybridized threats and threat actors called "The Com", "The Com Network", "The Community". The Com is a nebulous network of criminal activity and violent extremist focus chats and digital networks found across dozens of communication applications, where cyber criminals go to boast and recruit. The individuals and groups are not only increasingly violent, but also audacious enough to document and disseminate all their activities.
Brian Krebs described it as "[c]ollectively, this archipelago of crime-focused chat communities is known as “The Com,” and it functions as a kind of distributed cybercriminal social network that facilitates instant collaboration." According to an FBI affidavit:
Com consist of a geographically diverse group of individuals organized in various subgroups all of whom coordinate through online communication applications such as discord and telegram to engage in various types of criminal activity to include corporate intrusion, SIM swapping, cryptocurrency theft, commissioning in real life violence, and swatting.
Com is not a homogeneous community, rather it is a memeplex of digital criminal networks overlapping with gaming subculture. As Joseph Cox and Brian Krebs noted in past reporting the Com has existed for a while now, with the InfoSec community being aware of the network for their criminal activities. They use a diversity of messaging platforms to engage in widespread criminal acts.
The Criminological Pillars of Com
The Com network can be seen as having thee main pillars: Cyber Com, Sextortion Com, and Offline Com. There is a fluidity between the pillars of criminal activity and overlapping networks that are found within these pillars and individuals can be part of multiple communities simultaneously.
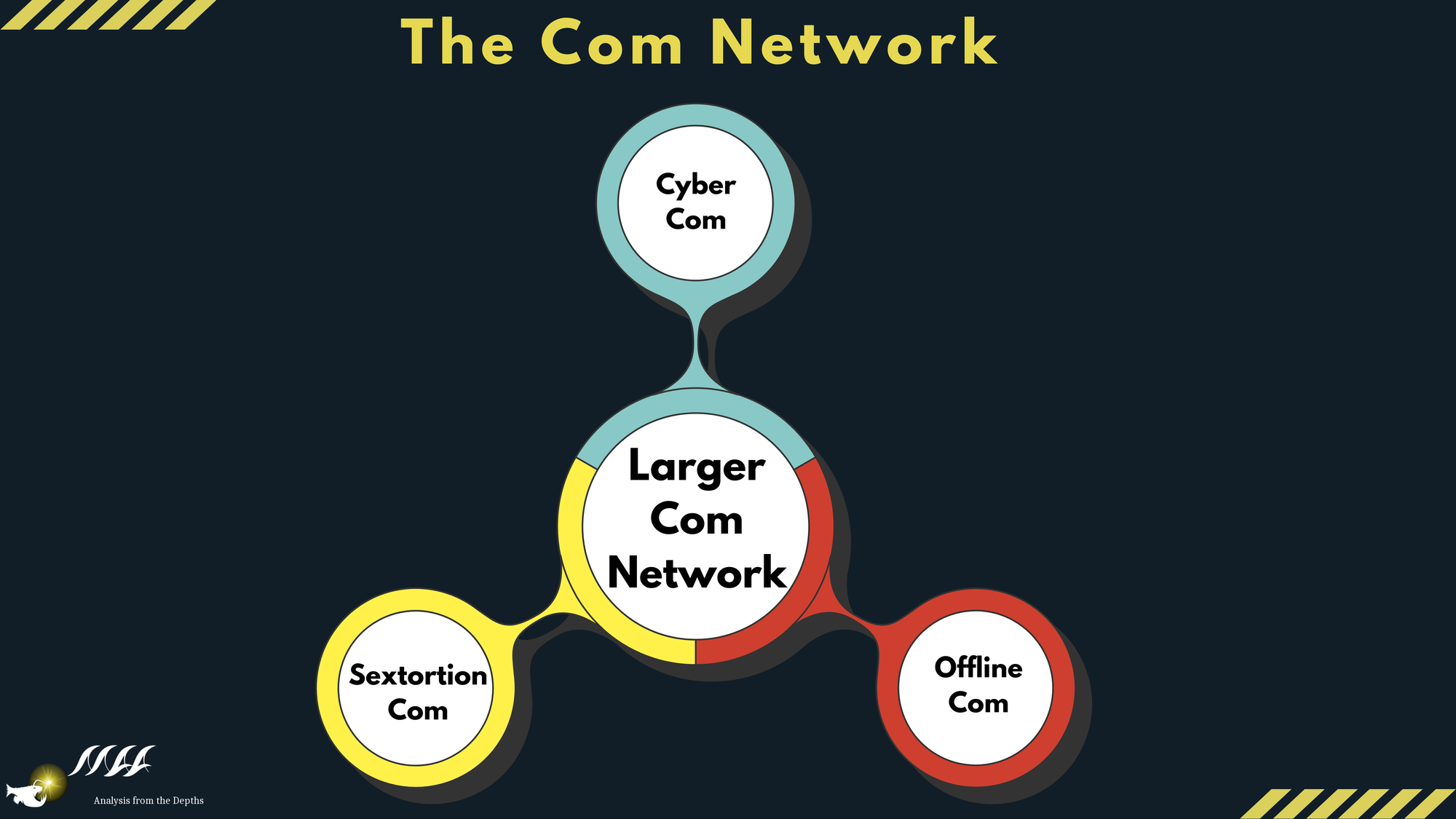
A) Cyber Com is the pillar of Com that is known for their cyber criminal activities such as: SIM Swapping, ransomware, swatting and social engineering data theft. Some of the recent popular cybercrimes incidents linked to Com are Snowflake-related breaches, and Scattered Spider.
B) Sextortion Com is the pillar of Com where members participate in extortion/sextortion. Members seek to persuade vulnerable and at risk minor into self-harm, sending sexually explicit images, and spread illegal content like CSAM and extreme gore videos. This network is associated with OSINT-based doxxing, social engineering and data dumping in efforts to create "lorebooks". LoreBooks are dedicated archives, which contain information dumps of personal identifiable information, as well as sexually explicit information about a specific individual, and are posted online for targeting the individual with malicious intent.
C) Offline Com is the pillar of Com focused on offline criminal activity ranging from: graffiti/vandalism, tire slashing, bricking, arson, random attack of strangers, stabbings, terrorism and bioterrorism. It features groups like Maniacs Murder Cult (M.K.Y.), No Lives Matter (NLM), and some segment of 764. Offline Com groups are accelerationist, occultic and national socialist in nature. Offline Com also overlaps with the True Crime Community, and minors within Com that are obsessed with school shooters.
Participation within these communities is also fluid. An individual from the swatting community might not be interested in consuming, producing or disseminating CSAM, however they have no qualms in offering swatting or doxxing and services in another user’s efforts to obtain material from a minor through sextortion, which results from the use of their swatting and doxxing services. Similarly, there is a fluidity between the criminal activity in Com and the national security threats also present in Com.
How Does it Function?
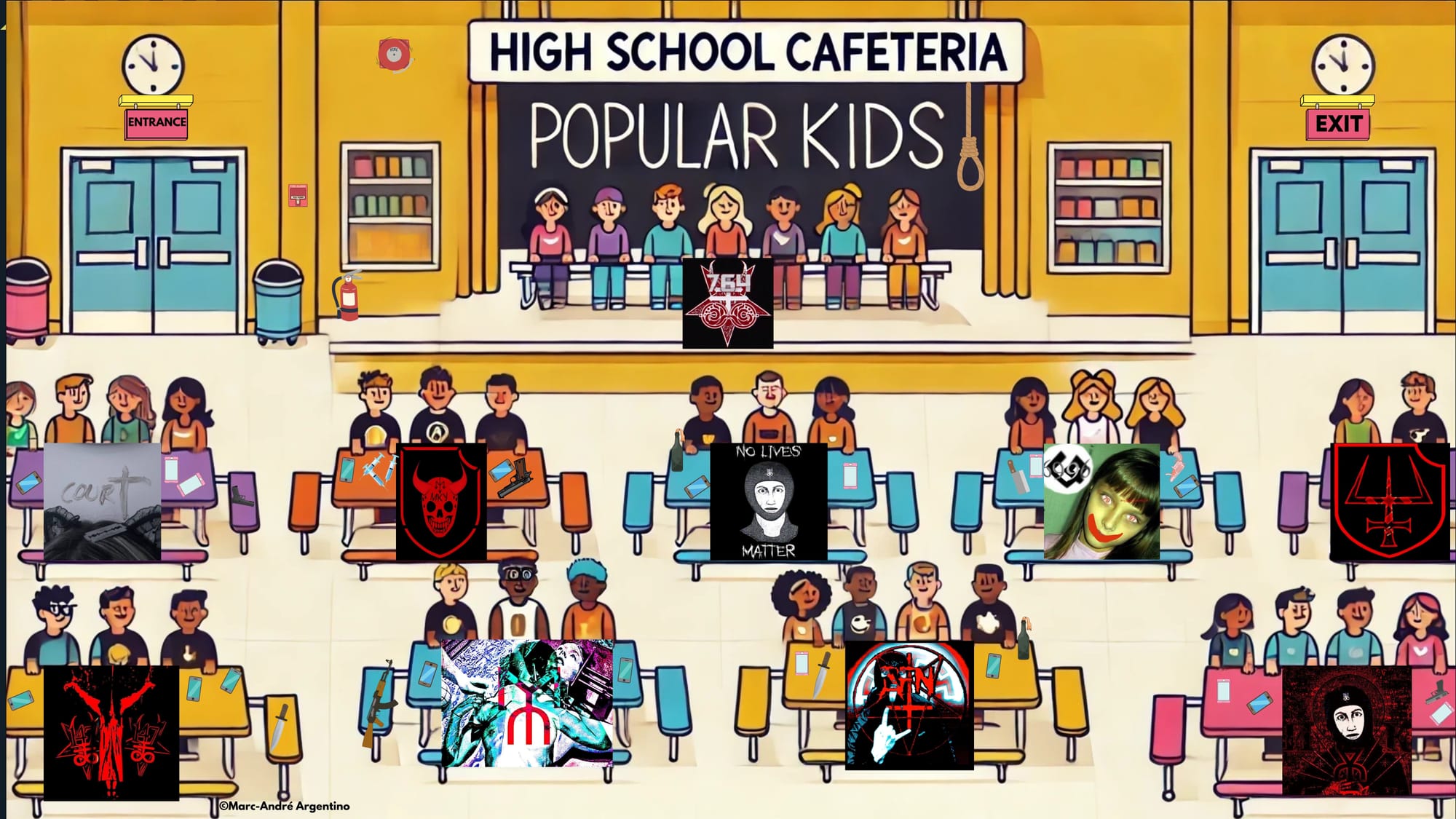
The fluidity between Cyber, Sextortion and Offline Com are like high school cafeteria tables, each defined by its own internal sociocultural dynamics. These groups might cluster around shared ideologies, but there’s a fluidity in how they interact and exchange ideas, reflecting the overlapping influences and evolving connections between them. The main way they cluster is by level of clout. Clout within Com operates like social standing among Com Groups. Just as popularity determines who sits at the "cool" table, the clout someone builds—through attention-grabbing violent actions or influence—dictates their rank and status in the network. Actions that gain the most recognition, like extreme violence, manipulating someone to commit suicide, or viral content of a member stabbing strangers, are akin to pulling off a daring stunt or being the star athlete, cementing an individual's place in the social hierarchy.
This clout becomes a currency, traded for respect, loyalty, and a higher position in the group. Just as teenagers might perform to impress peers or dominate the cafeteria social order, the teenagers in these networks chase clout through violent and criminal acts to secure their spot at the metaphorical "head of the table." It’s a competitive environment where the pursuit of recognition fuels increasingly extreme behavior. 764 is the most "influential" group within Sextortion and Offline Com, due to it being the singularity of the network and having the most infamous members. 764 has reached a mythical status withing the network, spawning hundreds of copycats and unofficial imitations. Other groups in the network compete for second place in terms of recognition and influence. This competition for attention and clout leads to an ever-growing escalation in the type of violent and criminal acts these minors are willing to perpetrate.
As violent acts gain attention and clout within the group, previously unthinkable actions become normalized. This sets a new baseline for what is considered acceptable or even praiseworthy behavior. A "one-upmanship" culture emerges where individuals or factions within the network try to outdo one another in terms of the severity or audacity of their actions. Their actions in this case are violent and sadistic in nature. Ultimately, over time, individuals in the Com network may require less justification to commit acts of violence. Smaller symbolic acts evolve into larger, more destructive events as action = membership, content = status and will get you on a groups roster (i.e. an invitation to the table so to speak). As members are exposed to more frequent and extreme violence, they become desensitized, reducing psychological barriers to further escalation. The escalation is often accompanied by increased dehumanization of perceived enemies, reducing empathy and moral constraints against violence.
To maintain or increase attention, individuals or groups often experiment with new methods of violence, leveraging novel tools, platforms, or strategies that maximize impact and shock value. They seek to take advantage of any avenue to chaos and escalation can also occur when extremist groups exploit chaotic or high-tension situations. High-profile attacks also have inspired imitation by others seeking similar recognition, further driving escalation.
In the end, what makes the Com Network so uniquely dangerous is the young age of the perpetrators and their blend of audacity and fluidity that defines its various criminal spheres. Members move freely between cybercrime, sextortion, and real-world violence—each domain acting as both a proving ground and a source of clout. The constant pursuit of recognition fuels a brutal cycle of escalation; extreme acts are celebrated, replicated, and intensified in a competitive race for notoriety. Over time, behavior that was once shocking becomes normalized, and the barriers to committing more serious offenses dissolve.
Far from being isolated or niche, the Com Network is a self-sustaining, multi-layered community whose influence is already visible in doxxing campaigns, swatting attacks, and disturbing real-world violence. Its online subculture, fused with extremist and criminal elements, accelerates the adoption of ever more harmful tactics. As groups like 764 gain near-mythical status within the network, they inspire legions of imitators eager for a slice of that infamy—making the threat not only persistent but actively expanding.